This is my first blog about computer hacking. I have debated for a long time if I should publish it or not. On a technical level, the vulnerability I discovered is not that complicated. There is no zero-day exploitation, no assembly code, no reverse engineering, or any crazy stuff people talk about on bug bounty programs.
Yet I still want to tell you my story. I want to show you that hacking is not all about writing complex scripts. Is about patience, imagination, and a little bit of luck. Hacking it a science, but also an art.
If you have read some of my blog posts, you know I'm a runner. In 2021, I bought a sports watch from a company called COROS. The brand is a rising star among distance runners. Elite athelets such as Eliud Kipchoge wears it to track heart rate, daily mileage, and other biometrics.
As a security researcher, I have a habit of looking up subdomains of some companies. In security this is called "asset discovery". Some companies may create a subdomain for internal use, but unintentionally expose the name to the public. It turns out, COROS made such a mistake.
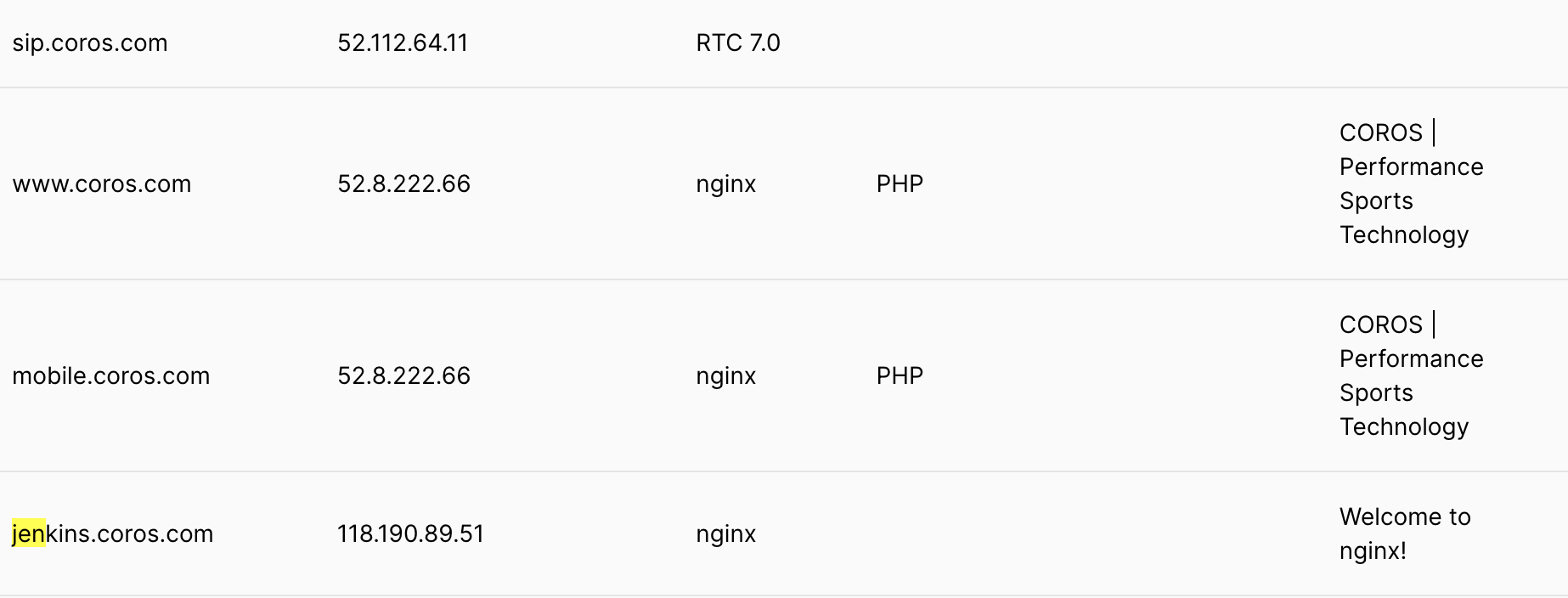
I used Pentest Tools to find subdomains. When I put coros[.]com into the search box, an interesting subdomain pops up -- jenkins[.]coros[.]com. Jenkins is an "open source automation server to support building, deploying and automating any project."
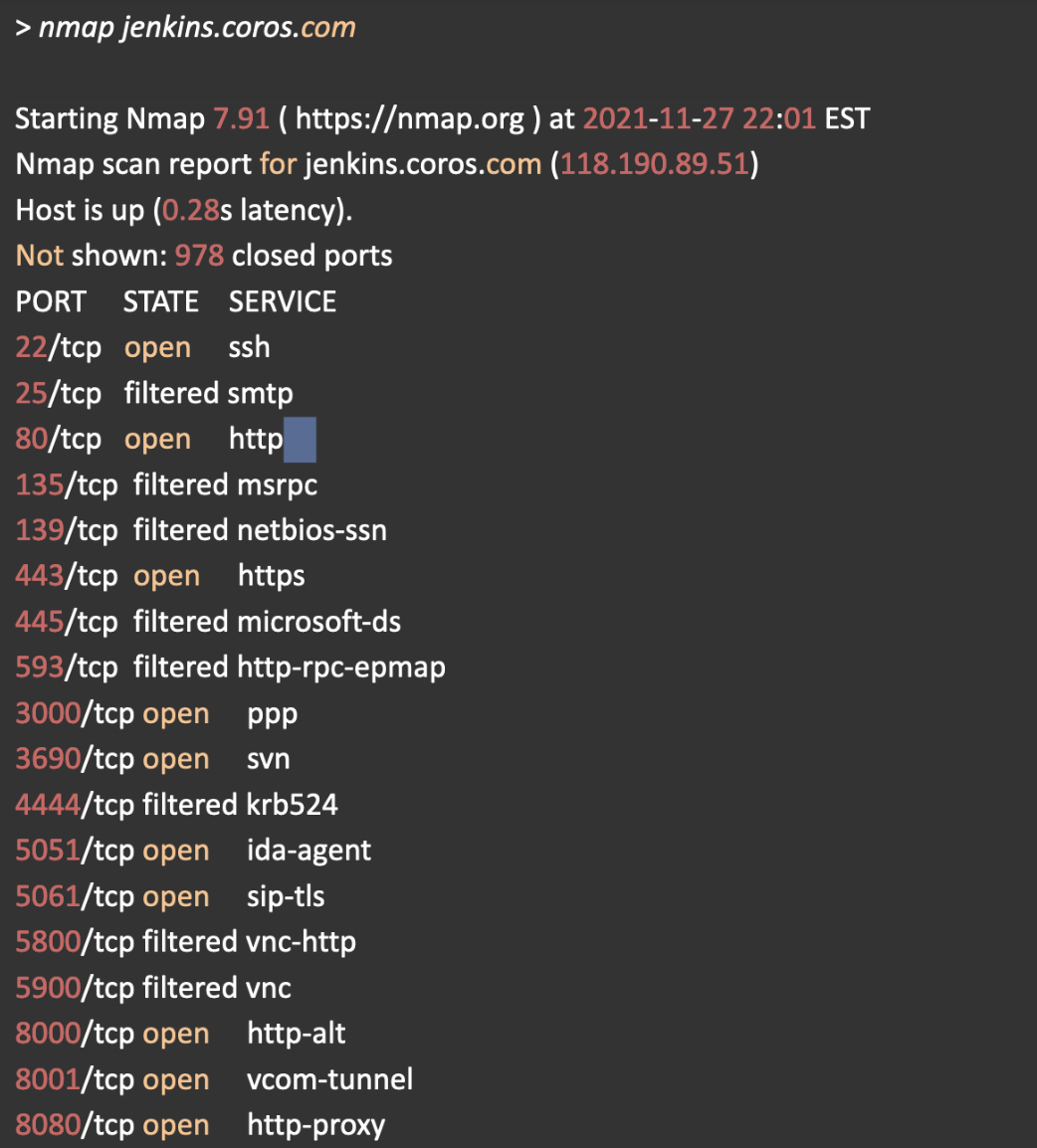
Was this subdomain used by developers? To learn more, I used nmap to discover open ports on this subdomain. The result is eye-opening -- 15 ports were open to the public.
Most ports are not interesting or are password-protected. After a lot of trial and error, I finally connected to port 3690, which runs the SVN server. SVN is a version control system similar to Github. For some reason, the developer did not add any password to the server! I suddenly realized that I have access to the source code running inside each COROS sports watch!
I immediately started to draft a vulnerability report to COROS. To assess the severity, I did a string search in the codebase to find any line of code with "password". I was shocked to find that the developer hard-coded username, password and hostname (URL) to connect to the database.
With the username and password, I was able to connect to the database. When I searched for my own name "Zhouhan", I found detailed entries about my running trips, heart beat, stride length, etc,. Since the watch is also used by elite athelets, I'm pretty sure their biometric data is also there...
I stopped searching. I asked myself -- how was that possible? If a developer added a firewall rule to only allow company IP to visit the subdomain, or if someone added password to the SVN server, I would not be able to discover anything substantial. A small mistake can lead to a serious incident.
So this is my hacking story. I was "somewhat technical" (knowing how to connect to a server, search for a string), imaginative (there are so many websites/targets out there, why COROS? because I'm a runner!), and lucky (what if a developer closed that port 1 day, 1 hour, or 1 minute after I started?).